- Published on
Secure Code Reviews That Prevent Breaches
- Authors

- Name
- Gabriel
- @gabriel__xyz
A secure code review is a systematic check of your application's source code to find and fix security flaws before they ever make it to production.
Think of it like a specialized inspection of a building's blueprint, but you're only looking for security risks before a single brick is laid. This proactive mindset is a non-negotiable part of modern, secure software development.
What a Secure Code Review Really Is
Most developers are used to standard peer reviews, but a secure code review looks at the code through a completely different lens. A typical code review checks for things like functionality, style, and logic. Does it work? Is it clean? A secure code review asks a much more pointed question: Can this code be exploited?
That shift in focus is everything. Instead of just making sure a feature works, the reviewer is actively hunting for weaknesses. They put on an attacker's hat, probing the code for common but dangerous flaws that automated tools often miss. Secure code reviews are a foundational piece of any solid suite of cybersecurity services, and they're crucial for staying ahead of new threats.
Core Goals of a Security-Focused Review
The main goal here is to harden your application from the inside out. When you scrutinize the source code, you're moving beyond just testing how the app behaves from the outside. You're getting to the root of potential problems.
The main goals include:
- Proactive Vulnerability Detection: This is the big one. Finding security weaknesses early in the development lifecycle is exponentially cheaper than fixing them after a product is live and a breach has occurred.
- Compliance and Standards Adherence: Many industries are bound by strict data protection regulations, like GDPR or HIPAA. Secure code reviews are a practical way to ensure your codebase meets these legal and industry standards.
- Cultivating a Security Mindset: When developers get involved in these reviews, they naturally start to think more defensively. The process builds a stronger, security-aware engineering culture where everyone feels a sense of ownership over protecting the application.
A secure code review is less about finding fault and more about building collective resilience. It's an educational process that elevates the entire team's ability to write safer, more robust code from the start.
Secure Code Review vs General Code Review
To really get why this is so important, it helps to see how a security review stacks up against a general peer review. While both are valuable, they have very different priorities.
One ensures the car drives well; the other ensures the airbags will deploy and the brakes won't fail.
| Aspect | General Code Review (Peer Review) | Secure Code Review |
|---|---|---|
| Primary Focus | Functionality, readability, and style | Vulnerabilities, weaknesses, and flaws |
| Main Goal | Ensure the code works correctly and is maintainable | Prevent security breaches and data exposure |
| Reviewer Mindset | Collaborative and constructive | Adversarial and investigative |
| Common Issues Found | Logic errors, performance bottlenecks, non-standard formatting | Injection flaws, broken authentication, improper error handling |
| Typical Outcome | A cleaner, more efficient codebase | A more resilient and hardened application |
Ultimately, a secure code review isn't just another quality gate; it's a critical defense mechanism. It transforms security from something you do after deployment into an integrated, proactive part of how you build software in the first place.
The Real-World Cost of Skipping Security Reviews

Treating secure code reviews as an optional checkbox is a gamble most businesses can't afford to lose. It's more than a technical hiccup; it’s a direct business risk with very real, high-stakes consequences. Insecure code is like a faulty foundation—the cracks might not be visible at first, but they’ll show when the pressure is on.
And when they do, the fallout can range from minor disruptions to catastrophic failures. We’re talking massive data breaches, serious financial hits, and brand damage that takes years to repair. A single, overlooked vulnerability can quickly turn into front-page news, wiping out customer trust and transforming a simple line of code into a multi-million dollar liability.
The Snowball Effect of Security Debt
This pile-up of unaddressed risk has a name: security debt. Much like financial debt, it starts small and feels manageable. Maybe a developer skips proper input validation to hit a tight deadline, or an old library with a known flaw is left unpatched.
Each shortcut seems minor on its own, but they compound. Over time, these small oversights snowball into complex, expensive messes that are exponentially harder to untangle. A fix that would have taken an hour during a code review can easily morph into weeks of work for an entire engineering team down the road.
Spotting these flaws early is where secure code reviews pay for themselves, contributing massively to long-term savings in software development. It’s the classic case of an ounce of prevention being worth a pound of cure.
From Minor Mistake to Major Breach
Attackers are masters at finding the path of least resistance, and seemingly minor mistakes are the wide-open doors they love to walk through. The modern development world, with its heavy reliance on public repositories, has only turned up the volume on this risk.
A recent analysis of public and private GitHub repositories found some alarming numbers. A shocking 35% of all repositories are openly accessible, making them a playground for attackers. Even more concerning, 61% of organizations have accidentally exposed secrets like cloud API keys in public code. That’s a massive, easily exploitable attack surface just waiting to be found.
Here’s how simple slip-ups escalate into major security incidents:
- Improper Input Validation: The classic SQL injection flaw. Without validation, an attacker can slip malicious code into a form field, tricking the database into handing over sensitive user data.
- Exposed API Keys: A developer accidentally commits an API key to a public GitHub repo. Automated bots scanning for these keys can find it in minutes, giving attackers a direct line to your cloud services, data, and infrastructure.
- Broken Authentication: Weak session management or flawed logic lets an attacker waltz past login screens, impersonate real users, and get their hands on private accounts and sensitive functions.
Skipping a secure code review is like skipping the final inspection on a parachute. It might seem fine on the ground, but you only discover the fatal flaw when it's too late to fix it. The cost isn't just financial—it's about reputation, trust, and operational integrity.
Ultimately, it’s clear that a secure code review isn't just a technical to-do list item. It's a critical business function that directly shields you from financial and reputational damage. When you connect insecure code to its real-world business impact, the case for making these reviews mandatory becomes undeniable. It’s an investment in resilience, ensuring your software is built not just to work, but to withstand a fight.
How to Conduct an Effective Security Review

Running a high-impact secure code review is more than just a quick scan for obvious bugs. It takes a systematic process, a bit of an adversarial mindset, and a laser focus on the corners of your code where vulnerabilities love to hide. Think of it less like proofreading and more like a detailed forensic investigation.
To really be effective, a reviewer has to put on an attacker's hat. They need to probe the code, asking tough questions about how data flows, where it's coming from, and how it’s handled before being shown to a user or stored in a database. Making that mental shift from a developer's perspective to a security analyst's is the secret to finding those deeply buried risks.
Establish a Systematic Inspection Process
A haphazard, "winging it" approach to secure code reviews is a surefire way to miss critical vulnerabilities. If you want consistent, thorough coverage, you need a structured plan. That means defining the scope, setting clear goals, and using a standardized checklist to guide every single inspection.
A well-defined process gets rid of the guesswork and makes sure every review, no matter who does it, meets the same high standard. This systematic approach is the backbone of any security program that can scale and be repeated reliably.
Your process should always nail these core steps:
- Define the Scope: Get crystal clear on what code is being reviewed. Is it a tiny new feature, a whole microservice, or a massive refactoring project? A tight scope keeps the review from becoming an overwhelming mess.
- Understand the Context: Get a bird's-eye view of what the code is supposed to do. What business logic is it handling? What are its inputs and outputs? This context is absolutely vital for sniffing out logic-based vulnerabilities that tools often miss.
- Manual and Automated Analysis: Get the best of both worlds. Use automated scanning tools (SAST) to catch the low-hanging fruit, then combine it with the nuanced, context-aware analysis that only a sharp human reviewer can bring to the table.
Focus on High-Risk Vulnerability Areas
Sure, every line of code matters, but let's be real—some areas are way riskier than others. By prioritizing these hotspots, you can focus your energy where it will make the biggest difference. Frameworks like the OWASP Top 10 are an excellent roadmap for knowing what to look for.
This focus is even more important with the rise of AI-assisted coding. A Veracode analysis found that around 45% of AI-generated code has at least one OWASP Top 10 security flaw, like cross-site scripting (XSS) or injection vulnerabilities. The OWASP Secure Code Review Guide offers a solid framework that covers the essential areas for finding these issues systematically.
A secure code review isn't about chasing perfection; it's about making a meaningful dent in your risk profile. By zeroing in on the most common and dangerous vulnerability patterns, you build a much stronger defense with the resources you actually have.
Key Areas to Scrutinize
To pull off a truly effective review, you have to know exactly where to look. A comprehensive checklist is your best friend here, ensuring no critical area gets overlooked. For a ready-to-use template, check out our detailed guide to building a code review checklist that your team can adapt.
Here are the essential checkpoints that need to be on every reviewer's list:
- Input Validation: This is your absolute frontline of defense. Scrutinize every single entry point where user-supplied data comes into the system. Is it being properly validated, sanitized, and type-checked to shut down injection attacks like SQLi or XSS?
- Authentication and Session Management: Dig into how users are verified and how their sessions are handled. Look for weak password policies, insecure session tokens, and sloppy logout procedures that could let an attacker hijack a user's account.
- Access Control: Once a user is authenticated, what are they actually allowed to do? Verify that the code enforces proper authorization checks on every single request, stopping users from getting their hands on data or functions they shouldn't be touching.
- Cryptography and Data Protection: Examine how sensitive data is handled, both in transit and at rest. Are strong, modern encryption algorithms being used? Or worse, are secrets like API keys and passwords just hardcoded right into the source?
- Error Handling and Logging: Vague or, even worse, overly detailed error messages can leak sensitive system info to attackers. Make sure error handling is robust, gives minimal information to the user, and that important security events are logged properly for later analysis.
By combining a structured process with a sharp focus on these critical areas, your team can turn secure code reviews from a simple quality check into a powerful, proactive defense mechanism.
Integrating Security Reviews into Your Workflow
Let's be honest: security can feel like a roadblock. Too often, it's that final, painful gate that slows everyone down right before a release. The goal is to stop treating secure code reviews like a last-minute chore and start weaving them into your team's natural rhythm. When you do, security shifts from a reactive headache to a proactive, everyday part of building great software.
The trick is to embrace the "shift left" mindset. It's a simple idea: move security checks as early into the development process as you can. When security is part of the workflow from day one, you spot vulnerabilities sooner, making them infinitely easier (and cheaper) to fix. This stops security debt from piling up and keeps your team moving fast.
Finding the Right Rhythm for Your Team
There's no magic formula for integrating security reviews. The right approach really depends on your team's size, the complexity of your project, and how much risk you're willing to stomach. The most successful teams I've seen blend smart automation with good old-fashioned human oversight.
- Manual Reviews on Pull Requests: This is your bread and butter. Before any new code gets merged, a designated reviewer (or two) gives it a security-focused once-over. This is perfect for catching tricky business logic flaws and complex vulnerabilities that automated tools just can't see.
- Automated Scans in CI/CD: This is your automated safety net. By plugging Static Application Security Testing (SAST) tools directly into your CI/CD pipeline, you get a powerful layer of defense. These tools automatically scan code on every commit or pull request, flagging common issues without anyone lifting a finger.
So, how do these pieces fit together? This simple flow chart breaks down the core stages of a well-structured secure code review.
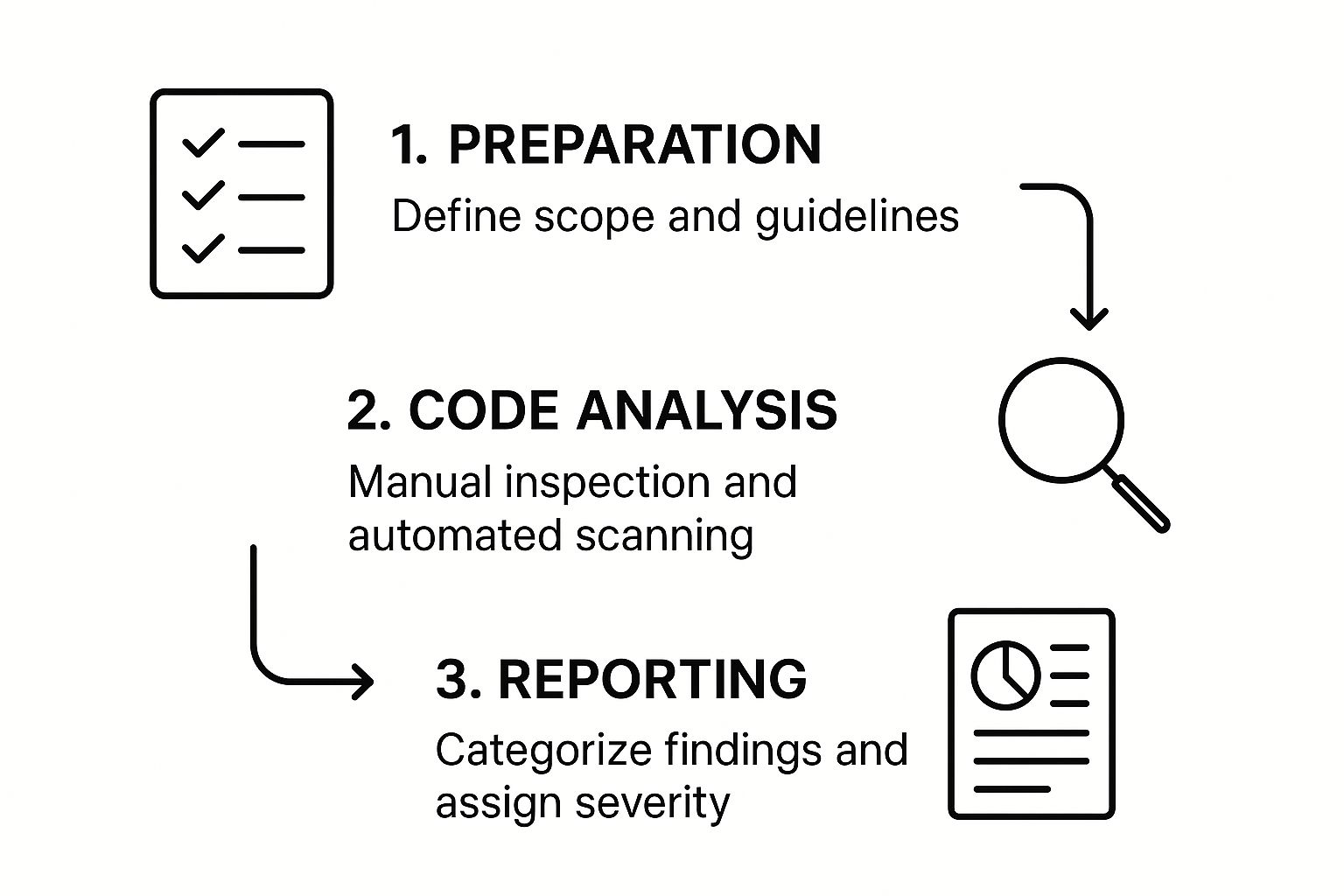
As you can see, a solid review process isn't random. It’s a systematic journey from clear preparation and analysis all the way to actionable feedback.
Blending Manual and Automated Approaches
Your strongest security posture will come from a hybrid model. Automated tools are incredible for speed and scale—they can tear through thousands of lines of code in minutes and never get tired of looking for known vulnerability patterns.
But they have a blind spot: they don't understand context. That's where your developers shine. A skilled engineer can spot subtle logic flaws, figure out if a flagged issue is a real risk or just a false positive, and grasp the business impact of a potential vulnerability.
A hybrid approach gives you the best of both worlds: the broad, fast coverage of automation combined with the deep, context-aware analysis of a human expert. It ensures you're catching both the low-hanging fruit and the complex, hidden risks.
To strike this balance, here’s a practical game plan:
- Start with Automation: Get a SAST tool embedded in your workflow right away. This gives you an immediate baseline of security coverage and provides developers with instant feedback. You can learn more about setting this up with our guide to code quality checks with GitHub Actions and Slack.
- Define a Manual Review Cadence: Not every line of code needs the same level of scrutiny. Mandate manual secure code reviews for changes touching critical areas like authentication, payment processing, or sensitive data handling. For lower-risk changes, an automated scan might be enough.
- Create a Security Champions Program: Find the developers on your team who are genuinely passionate about security and empower them. These "security champions" can become the go-to experts for their colleagues, lead manual reviews, and help sort through the findings from automated tools.
- Make It Collaborative: Build a culture where security is a shared responsibility, not just one person's job. The point of a review is to make the code better, not to point fingers.
By making secure code reviews an integrated and collaborative part of your daily work, you build a more resilient development process—one that actually boosts your protection without killing your momentum. This transforms security from an obstacle into an enabler of speed.
How AI and Automation Are Changing Code Security
 The world of secure code reviews is going through a massive shift, and it’s all thanks to AI and automation. While manual reviews are still gold for catching business logic flaws, they’re slow and just can’t keep up. Today's security pace demands something faster and more scalable, which is exactly where AI-powered tools are stepping in.
The world of secure code reviews is going through a massive shift, and it’s all thanks to AI and automation. While manual reviews are still gold for catching business logic flaws, they’re slow and just can’t keep up. Today's security pace demands something faster and more scalable, which is exactly where AI-powered tools are stepping in.
These aren't your old-school vulnerability scanners that just match signatures from a list. Modern tools use machine learning to actually understand code. By analyzing huge datasets of both good and bad code, they learn to spot complex exploits that a human reviewer might easily skim past.
Augmenting Human Expertise, Not Replacing It
Let's get one thing straight: AI isn't here to make security experts obsolete. It's here to make them better. AI and automation act as a powerful force multiplier, taking on the tedious, repetitive work so developers and security analysts can focus on the bigger picture.
Think of an AI security tool as the world's most dedicated junior reviewer—one that never gets tired or bored. It can blaze through thousands of lines of code, flagging common issues in seconds. This frees up your senior engineers to hunt for the tricky, context-specific vulnerabilities that require a human brain.
The money trail confirms this shift. The market for secure code review platforms is currently sitting around USD 1.22 billion and is on track to hit USD 2.44 billion by 2030. A huge chunk of that growth is coming from AI-augmented tools, which are popular for their knack for reducing false positives and even suggesting fixes. For more on that, check out this secure code review platforms market report.
To better understand where each approach fits, it helps to compare them side-by-side. Traditional manual reviews offer depth, while automated tools provide speed and scale. AI-augmented reviews aim to blend the best of both.
Comparing Manual vs Automated Security Reviews
| Attribute | Manual Review | Automated Review (SAST) | AI-Augmented Review |
|---|---|---|---|
| Speed | Slow, hours to days | Fast, minutes | Very fast, real-time |
| Accuracy | High, but prone to human error | High for known patterns, lots of false positives | High, with reduced false positives |
| Scalability | Low, limited by team size | High, scans entire codebase | High, scales effortlessly |
| Cost | High, requires expert time | Moderate, subscription fees | Moderate to high, depends on features |
| Context | Excellent at business logic | Lacks context | Good, getting better at context |
| Best For | Critical business logic, complex vulnerabilities | Finding common flaws (OWASP Top 10) | Real-time feedback, scaling security |
Ultimately, the strongest security posture comes from a hybrid approach. Use automation to catch the low-hanging fruit and lean on human expertise for the complex, high-stakes reviews.
The Rise of Real-Time Security Feedback
Maybe the biggest game-changer from automation is how it brings security directly into the developer's workflow. Modern tools don't wait for a formal review; they plug right into IDEs and CI/CD pipelines to give feedback as code is being written.
Instead of waiting days for a manual review, developers get real-time alerts about potential vulnerabilities, complete with context and suggested remediations. This immediate feedback loop is crucial for building a security-first culture.
This proactive style has some serious perks:
- Reduces False Positives: AI models are getting much better at understanding code context, which cuts down on the "noise" and false alarms that plague older static analysis tools.
- Suggests Code Fixes: Many tools don't just point out problems—they offer secure code snippets to fix them, speeding up remediation and teaching developers good habits along the way.
- Scales Security Efforts: Automation makes it possible for every single pull request to get a baseline security scan, something that’s just not feasible with manual reviews alone.
By adopting these technologies, you can build a security program that’s more efficient, scalable, and just plain stronger. To see what this looks like in the real world, check out our list of the 12 best code review automation tools for 2025. This is how you prepare your team for a future where security is a natural part of development, not a roadblock.
Frequently Asked Questions About Secure Code Reviews
Even with a solid plan, questions always pop up when you start doing secure code reviews. This section tackles the most common ones we hear, giving you straightforward answers to get your team on the right track.
Think of it as the final check on your security strategy. Getting these details right is what makes a review process stick—and actually work.
How Often Should We Perform Secure Code Reviews?
There’s no magic number here. The right frequency really depends on how critical the code is. A tiered approach is usually your best bet.
- For High-Risk Components: Anything that handles authentication, payments, or sensitive user data needs a secure code review on every single pull request. No exceptions. This is a non-negotiable step to keep your most important assets locked down.
- For Lower-Risk Areas: For less critical parts of your app, you can strike a balance. Combine automated scanning on every commit with periodic manual reviews—say, quarterly or before a big release. This gives you a good mix of security and speed.
The real goal is to make it a routine. Every piece of code should face some form of security check before hitting production, whether it's manual or automated.
The best security programs don't treat reviews like a special occasion. They make them a normal, everyday part of building software. Consistency beats intensity every time.
Who Is Responsible for Conducting the Review?
Secure code review is a team sport, period. It's tempting to lean on a single security champion or someone from the AppSec team, but that creates a bottleneck and a single point of failure.
A much healthier approach involves a few key players:
- Peer Reviewers: Get developers from the same or neighboring teams involved. The reviewer should never be the person who wrote the code—you absolutely need a fresh set of eyes to spot mistakes the original author might have missed.
- Security Champions: These are the developers on your team who are passionate about security. They can offer a deeper look and help mentor others, which helps security knowledge spread organically.
- Automated Tools: These are your first line of defense. They catch the low-hanging fruit and common vulnerabilities, freeing up your human reviewers to hunt for the tricky, context-specific bugs.
When everyone shares ownership, the review quality skyrockets. More importantly, it helps build a stronger security mindset across the entire engineering team.
What Is the Difference Between a Secure Code Review and a Penetration Test?
This is a big one. People often mix them up, but they’re two very different—and equally vital—security activities. They aren't interchangeable; they work together.
Think of it like inspecting a castle’s blueprints versus trying to storm its walls.
A secure code review is a "white-box" test. The reviewer gets full access to the source code, diagrams, and documentation. They’re looking for flaws from the inside out, like a building inspector checking the foundation and wiring before the walls go up.
A penetration test, on the other hand, is a "black-box" test. The tester acts like a real attacker, hitting a live application from the outside with no inside knowledge. Their goal is to find and exploit vulnerabilities from an external perspective.
You need both. A code review might find a weak encryption algorithm, while a pen test might discover a misconfigured server that’s leaking data. A truly strong security posture relies on both perspectives.
Ready to eliminate pull request noise and accelerate your development cycle? PullNotifier integrates seamlessly with GitHub and Slack to deliver clean, real-time PR updates, cutting review delays by up to 90%. Start streamlining your workflow for free today.